 Server problems usually come unexpected and surprise you when you least expect it. In order to initiate the right measures immediately, you have to know many factors and be able to access them as quickly as possible. But with many systems the use cases increase and you come to a point where you are quickly overwhelmed with what is suddenly at your feet as a task.
Server problems usually come unexpected and surprise you when you least expect it. In order to initiate the right measures immediately, you have to know many factors and be able to access them as quickly as possible. But with many systems the use cases increase and you come to a point where you are quickly overwhelmed with what is suddenly at your feet as a task.
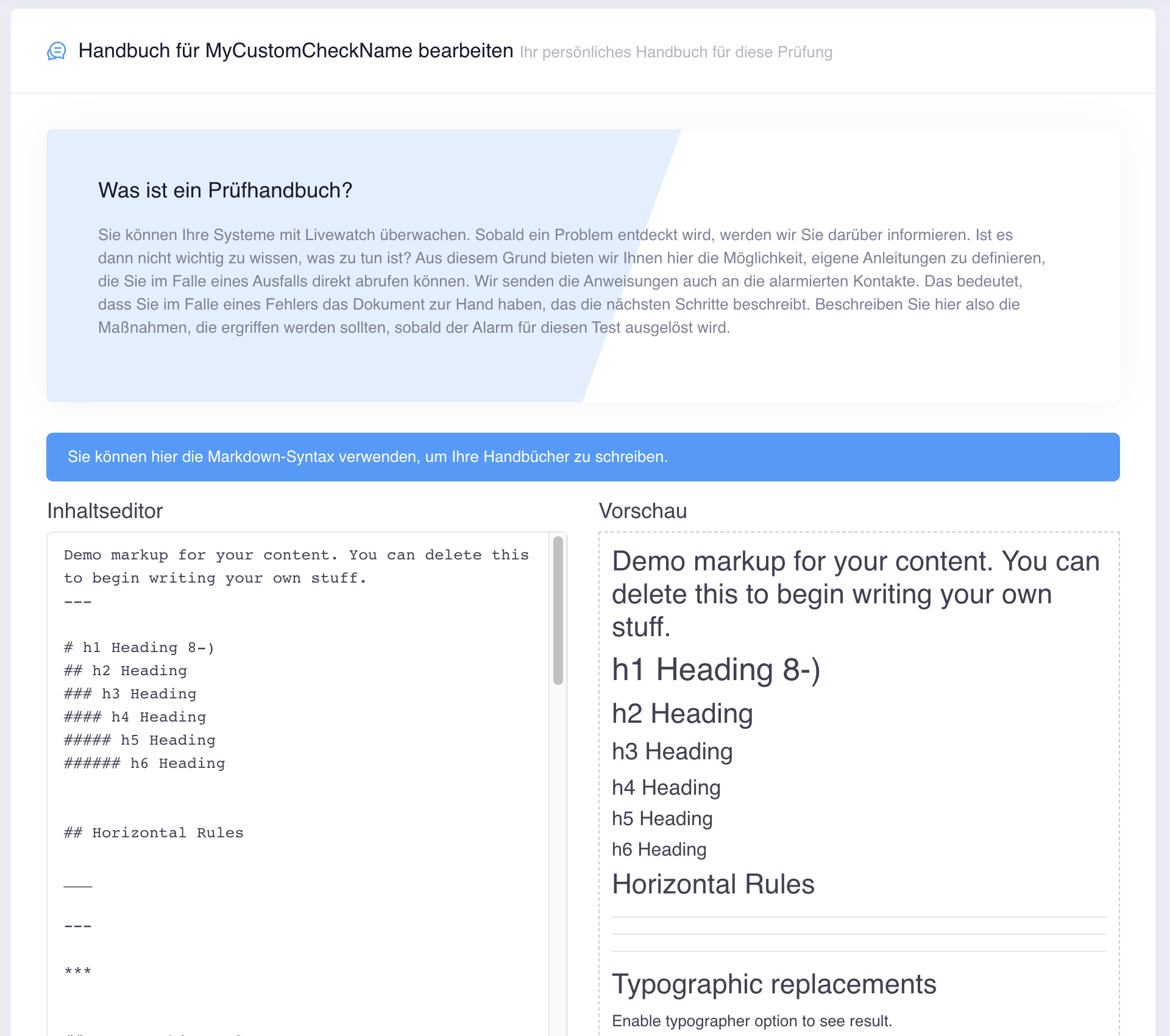
It would therefore be easy if the most important steps to be dealt with in the event of a malfunction were described in advance and were immediately available in the event of a particular incident.
Livewatch now offers you the option of creating manuals for your checks, in which you can note down the most important steps. Briefly describe the measures to be taken in the event of a fault. As soon as Livewatch detects an outage, you can access these documents immediately and know what to do.
In the Livewatch customer area, you now have the option of creating manuals for each check and adapting them to the new requirements at any time. In this way, all users contacted can immediately and easily receive the most important information about your check.
Here we answer questions about server monitoring from Livewatch. If you have a question that we have not yet answered here, please contact us.
In recent months, several critical security vulnerabilities have been discovered in server systems that can potentially have serious consequences for IT security. Some of the most significant vulnerabilities are presented below:
1. CVE-2024-37079: Security vulnerability in VMware vCenter Server
In June 2024, a critical vulnerability was identified in VMware vCenter Server. This vulnerability allows attackers to execute arbitrary code using manipulated packages, leading to a heap buffer overflow and endangering services. VMware has already released a patch that should be installed urgently.
2. CVE-2024-49113: LDAPNightmare in Windows servers
A recently discovered vulnerability in the Windows Lightweight Directory Access Protocol (LDAP) implementation, known as CVE-2024-49113, allows attackers to cause a denial-of-service (DoS) condition by crashing the Local Security Authority Subsystem Service (LSASS). Microsoft fixed this vulnerability in December 2024.
3. CVE-2024-20697: Vulnerability in Windows 11 and Server 2022
A vulnerability in Windows 11 and Windows Server 2022 allows attackers to execute arbitrary code when extracting RAR files. Microsoft fixed this vulnerability in January 2024 and recommends installing the patch and avoiding opening RAR files from unknown sources.
4. CVE-2024-21410: Critical vulnerabilities in Microsoft Exchange servers
The Federal Office for Information Security (BSI) reported in March 2024 that at least 17,000 instances of Microsoft Exchange servers in Germany are vulnerable to critical vulnerabilities. These gaps are already being actively exploited by cyber criminals. The BSI recommends using current versions of Exchange, installing available security updates and configuring the instances securely.
5. CVE-2024-49112: Zero-day vulnerability in Windows and Windows Server
A zero-day vulnerability in Windows and Windows Server enables denial-of-service attacks because it causes the operating system to crash. Windows 10, Windows 11 and Windows Server 2016, 2019 and 2022 are affected. Microsoft fixed this vulnerability in August 2024.
A push notification is an automatic message sent by an application or service to a device without the application being actively open on the device. These notifications are "pushed" or actively sent from the server to the client, rather than the client actively checking for updates.
Here are some important features of push notifications:
Active delivery: Push notifications are sent from the server to the device without the app or browser actively running. This allows important information to be sent to the user immediately, even when the app is in the background or closed.
Direct Communication: Push notifications enable direct communication between the server and the user's device. This is particularly useful for notifying users of events, updates, or relevant information.
Adjustable permissions: Users typically have control over which apps or services are allowed to send push notifications. This ensures that users are not bothered by unwanted notifications.
Different Platforms: Push notifications are supported on different platforms such as iOS, Android and Web. The implementation may vary depending on the platform, but the basic concept remains similar.
Versatile Application: Push notifications are used in a variety of applications including messaging apps, social media, email, news apps and more. They are an effective way to keep users informed of updates and relevant information.
Examples of push notifications are:
Message notifications: Notifications about incoming messages in messaging apps.
Updates: Notifications about software or app updates.
Events: Notifications about upcoming events, appointments or activities.
It is important that push notifications are used responsibly to ensure a positive user experience and not overburden users. Users should also have the ability to customize push notification settings based on their preferences.